You have learnt how to create your AWS account, now it’s time to learn some highly recommanded best practices to secure your AWS account, let’s start:
1. Activate Multi-Factor Authentication on root account
For this, login to aws management console at: https://console.aws.amazon.com/, select “Root user”, enter your email account then clic on next, then provide your password.
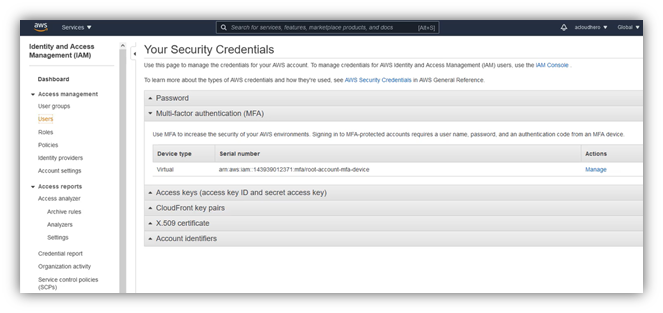
At the top left, clic on “Services”, then search for category: “Security, Identity & Compliance”, then clic on IAM.
Clic on “Add MFA”.
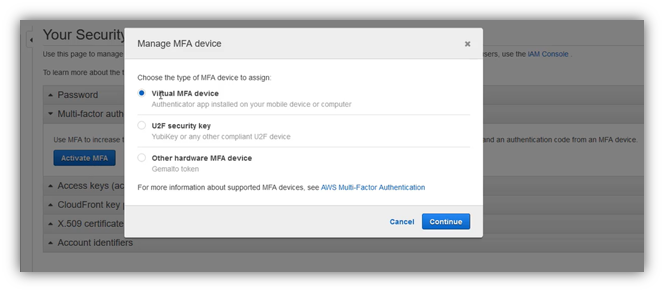
AWS allows you to use multiple types of multi-factor authentication options:
- Virtual MFA devices: This is the most popular option among architects and developers, and you can use mobile applications like Google authenticator, Authy, and Virtual MFA devices.
- U2F security keys: This is an external device that can be plugged into your laptop to authenticate.
- Hardware Key Fob MFA Devices
Clic on “Activate MFA”, a new window will be displayed, choose “Virtual MFA device” then clic on “Continue”
 For me, I have already installed Google Authenticator app on my mobile phone, you can follow this article to install and configure Google Authenticator: Get verification codes with Google Authenticator
For me, I have already installed Google Authenticator app on my mobile phone, you can follow this article to install and configure Google Authenticator: Get verification codes with Google Authenticator
Open Google Authentication app and scan the QR code displayed, then enter two consecutive generated MFA codes.
Clic “Assign MFA”
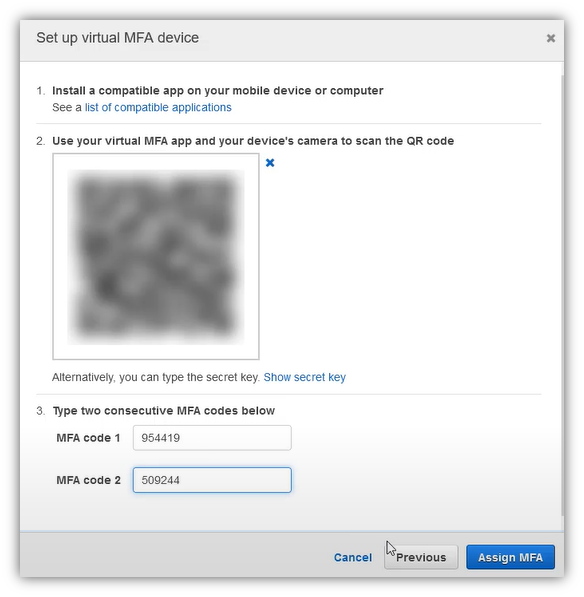
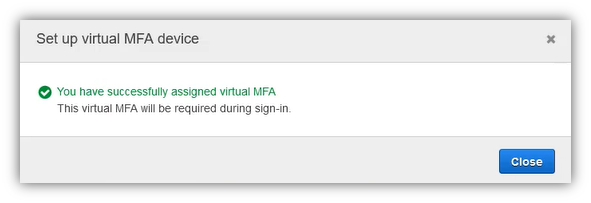
If all is ok, you will get a message informing you that virtual MFA is assigned successfully.
2. Create a new IAM user with administrator priveleges:
In IAM Service, clic on “Access management” then “Users”:
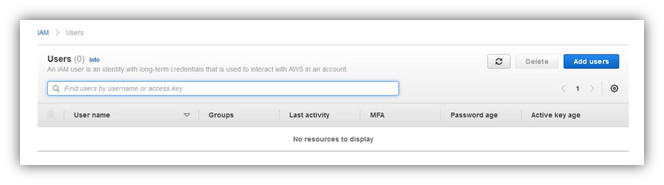
 Clic on “Add user”;
Clic on “Add user”;
A new page displayed where you will add your username, in my case, I have entered: “admin” which I will use for daily aws tasks.
Select both credentials types:
- Access key – Programmatic access, this enables an access key ID and secret access key to be used for AWS API, CLI, SDK and other dev tools.
- Password – AWS Management Console access: it enables a password that allow users to sign-in to the AWS Management Console.
You can auto-generate a password, or select Custom password and enter your password.
Then, if the account will be used by another person, I highly recommand to select “User must create a new password at next sign-in”
Then clic on “Next Permission”
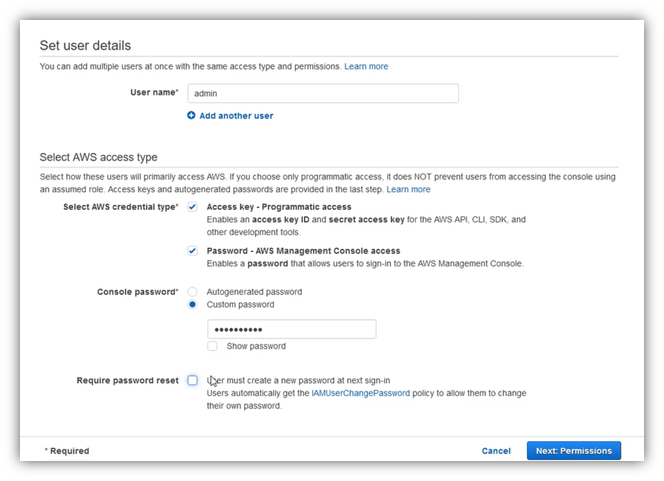
Clic on “Attach existing policies directly”, then on the policies, select “AdministratorAccess”, and clic “Next: Tags”
Leave the tags page blank and clic on “Next – Review”:
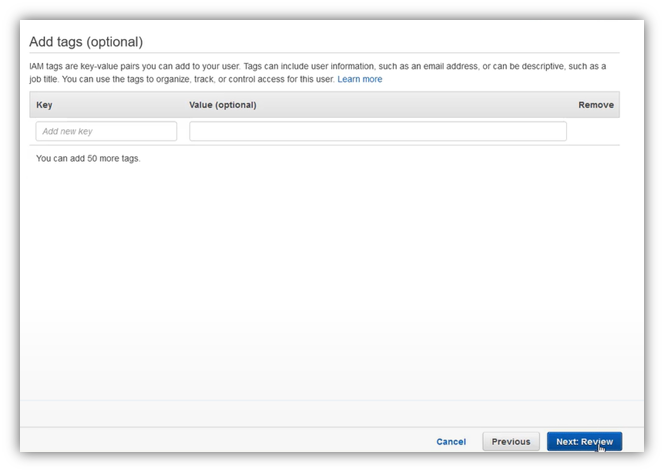
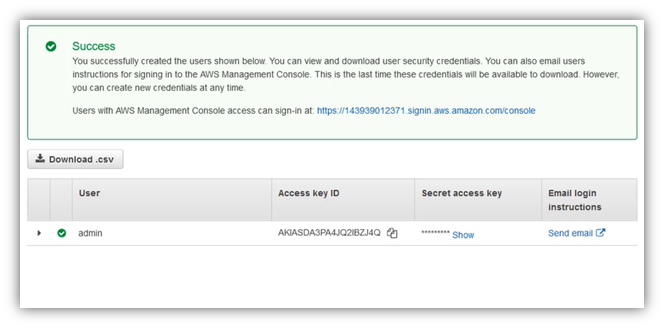
Review your choices, then clic on “Create user”:
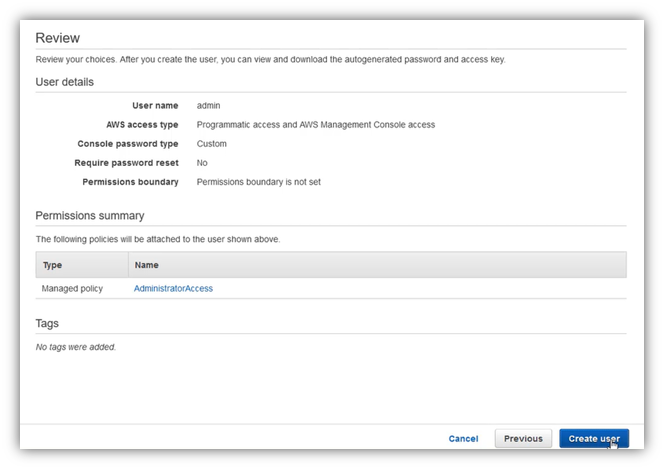
Once user is created, you can download the csv file containing your Access Key ID and Secret Key ID, you can also sign-in to AWS Management Console related to your account using username and password you have entered in previous steps:
3. Setting up Password Policy:
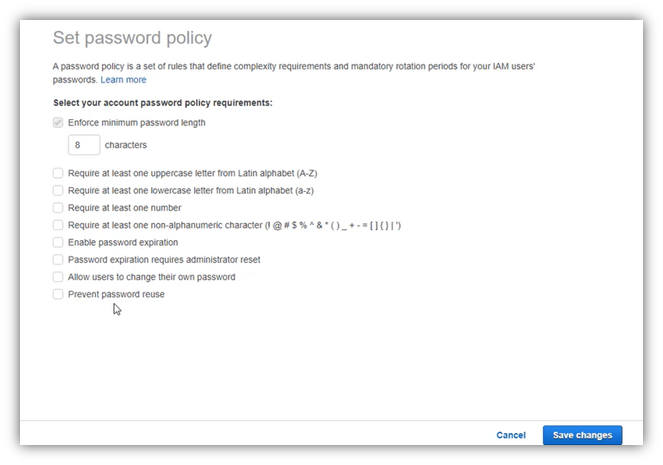
A good password policy, must at least respect the following:
- Minimum password length is 8 characters
- Includes at least one character of each the four types: uppercase, lowercase, number and special character:!$#@-()…
- Must not be identical to your AWS account name or email address.
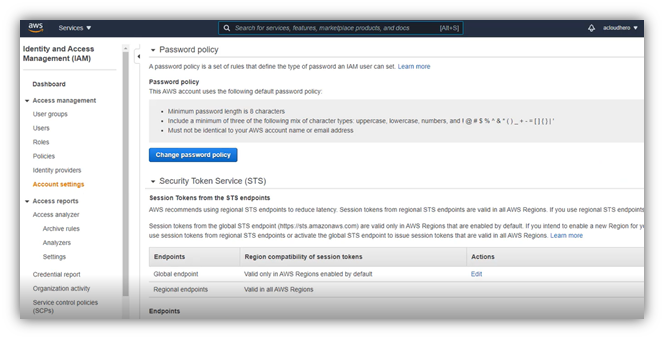
Open IAM service, and on the left menu, clic on: “Access management” / “Account settings” , then clic on “Change Password Policy”:
Choose all password characteristics that you want all users respect, then clic on “Save changes”
Congratulation, you have now secured your AWS account, you can now, jump to this article in order to explore the AWS management console.
